Progress of Information Technologies
Progress in the field of information technologies, software development, and the formation of personal databases has significantly heightened the problem of information protection.
Businesses must ensure their clients that personally identifiable information and personal data are protected from hackers and third parties attempting to gather that information.
Types of Data
There are two main types of data classification – Personally Identifiable Information (PII) and Personal Data. PII is the term used in the USA, while the term personal data is generally described in the European Union.
Both terms classify information that can directly or indirectly reveal an individual’s identity (name, address, phone number, passport, driver’s license, financial information, medical records, etc.)
Privacy Information Laws
Several data protection laws have been enacted in various countries to provide guidelines for companies that collect, store, and share personal information about customers.
- GDPR – The General Data Protection Regulation is a European Union regulation on data protection and privacy in the EU and the European Economic Area (2018).
- CCPA – The California Consumer Privacy Act is a state statute intended to enhance privacy rights and consumer protection for residents of California, United States (2018).
- PIPEDA – The Personal Information Protection and Electronic Documents Act is a Canadian law relating to data privacy (2000).
- LGPD – The General Personal Data Protection Law is a statutory data protection and privacy law in the Federative Republic of Brazil (2020).
The basic principles in these laws indicate that certain confidential information may not be collected or shared with third parties except as provided by law.
CRM Data Protection
As data security and privacy compliance come to the fore, data protection plays an essential role in meeting fundamental security requirements. Especially for CRMs, as they collect large amounts of identity, descriptive, quantitative, and qualitative data: contacts, leads, accounts, cases, deals, opportunities, activity, performance, and more. How to protect these data?
For example, while working in CRMs’ non-production environments?
Microsoft has made this extremely easy with an instance manager that allows you to copy a working instance. But do you have the right to use your customers’ personal information? You must protect sensitive information so that development teams can work securely.
Or, if you want to analyze your customers’ behavior and you need to transfer data from CRM to third-party providers? They will see the test results and medical records of patients if we are talking about CRM data of the medical institution. Or they will see the addresses, purchase lists, and spending amounts if we are talking about e-commerce CRM. What to do in this situation to protect information?
One solution is data masking.
Data Masking
Data obfuscation (masking) is a data protection method that encodes data to hide the actual values using fake content like characters or numbers. It protects the process of transferring files from one place to another. It also helps ensure CRM development, testing, debugging, analysis, or migration.
To achieve data masking in CRM and to not lose source data, it is essential to create a copy of the database that corresponds to the original. When a query is directed to the database, records are replaced with dummy data, and masking procedures are applied accordingly.
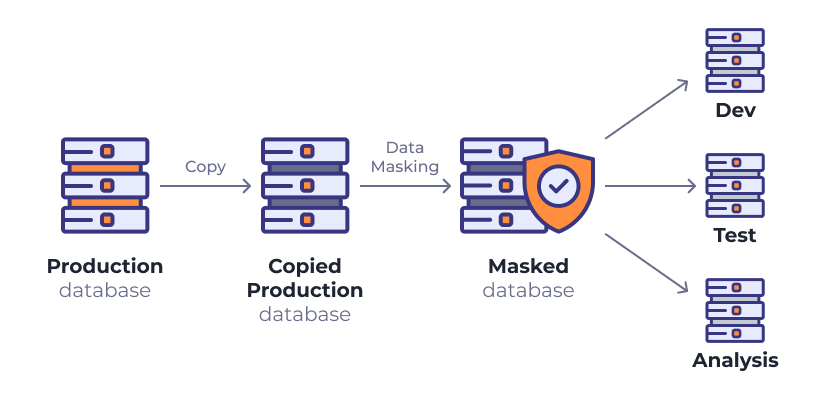
Data are one of the significant assets of organizations. Data masking preserves the structure and format of the original data, making it an ideal technique to aid in non-production procedures, research, and analysis.
In most masking tools, there is no possibility to reverse back the source data, so pay attention to making a copy before starting the masking process.
A Few Facts
Penalties for non-compliance with data privacy laws (maximum fines):
UDS Systems has created UDS Business Data Masking , a free application that helps you protect personal information, protect your reputation, and save your money.

